SEEK LESS, FIND MORE.
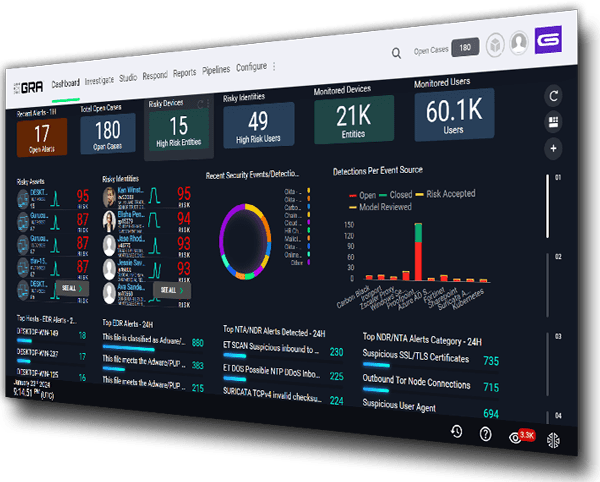
Radical Threat Clarity Delivered Day One
Dynamic Security Analytics Out-of-the-Box
Unlock the converged capabilities of Next-Gen SIEM, UEBA, XDR, Identity Access Analytics and SOAR for actionable insights and effective threat detection, investigation and response.
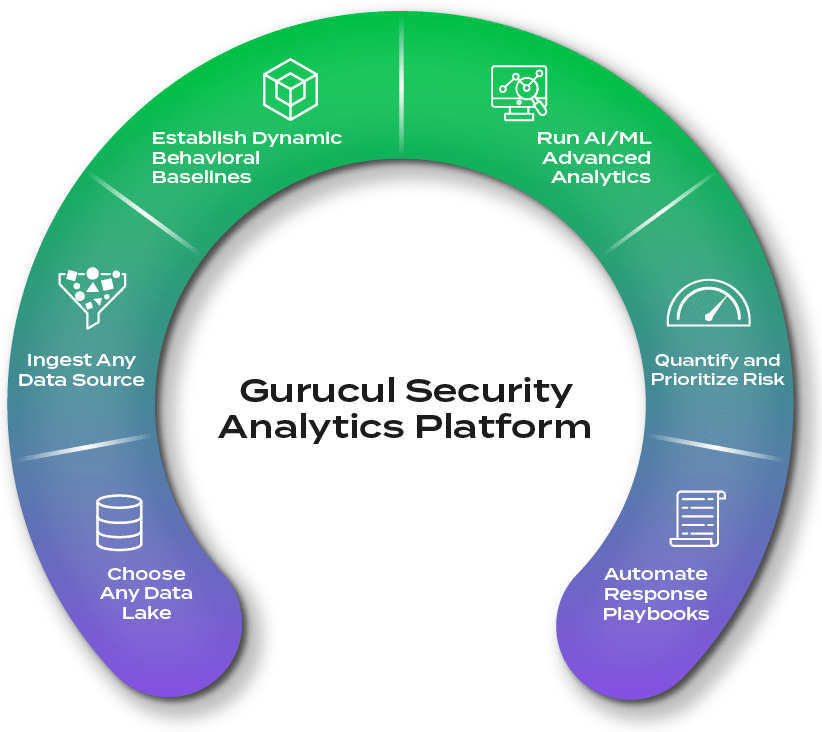
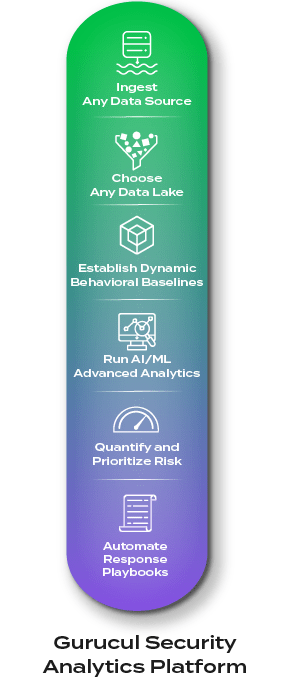
Don’t compromise. Gurucul’s cloud-native, dynamic security analytics platform adapts to YOUR enterprise, giving you nearly unlimited choices in how you architect and deploy it, integrate it with your tech stack and scale for growth.
Ensure full visibility. Gurucul’s intelligent, ML-powered data fabric automates data ingestion and interprets, monitors, enriches, reduces and routes data from any source, format or IT estate, even non-security related data for full visibility and coverage.
The best of both worlds. Go from data ingestion to high-fidelity detections in seconds. Our massive library of pre-built security content is fully enabled OOTB to deliver high value detections right away while allowing easy customization to your environment.
From data to insight. Find true positives in real-time with our library of 3,000+ ML models. They can be chained together to trigger, confirm, filter and cross-validate alerts, finding the unknown unknowns and surfacing what matters most.
Prioritize what matters most. Quantify and elevate business risk specific to your enterprise using our customizable, dynamic risk engine. It adjusts in real-time, normalizes scores, and can be adapted to any risk framework.
Combat sophisticated threats. Benefit from native, secure AI that works on the front and back end to reduce MTTD and MTTR. Behind the scenes: Our AI is constantly improving the efficacy of our detections, creating new models and suggesting response playbooks. For analysts and responders, it uses natural language search and queries to streamline investigations and hunting.
For SOC Teams
Empower SOC analysts with accurate, contextualized detections and AI at their fingertips.
For Insider Threat Teams
Predict risks destined to become threats with unparalleled behavioral-based analytics.
Proven Business Benefits from Gurucul Customers
Those Who Know, Know Gurucul
Hear from some of our customers
Featured News & Resources
Gartner Report
Learn why Gurucul ranked in the top 3 for all SIEM use cases in the 2022 Gartner® Critical Capabilities for SIEM report
2023 Insider Threat Report
Report from Cybersecurity Insiders shows insider attacks are becoming more frequent and harder to detect
AI TDIR Use Case Report
If the secure and strategic application of AI into SecOps is a priority for 2024 this Gartner Emerging Tech report is a must-read.




