Dynamic Security Analytics Platform
Delivering Radical Clarity Into Your Cyber Risk
Gurucul’s dynamic security analytics platform helps you uncover true threats and quantify cyber risk across your entire IT estate. It provides real-time prioritized and actionable insights so you can spend more time on what’s most important, quickly eradicating threats.
Dynamic Security Analytics Platform
A cloud-native platform steeped in data science with unified analytics capabilities. No need for siloed tools that don’t provide a clear picture of your risk.
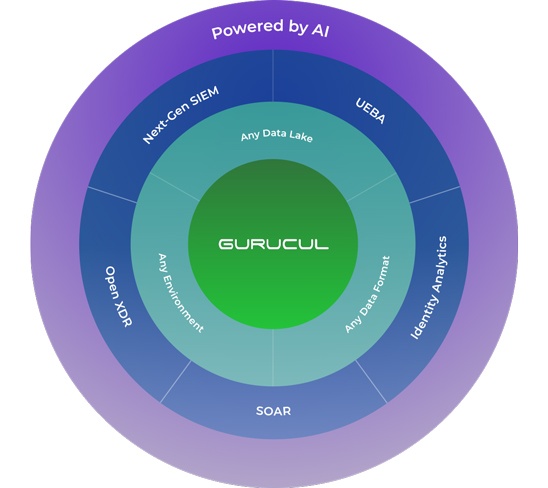
Gurucul is an open and adaptable big data platform that gives you nearly unlimited choices in how you deploy it, integrate it with your business processes and tech stack. The platform is built for speed and scale to handle demanding workloads with an architecture that can scale dynamically.
Gurucul’s Security Analytics Platform enables you to ingest, search and analyze any Security and IT Ops data you need, regardless of the format, source or IT estate. This means you’re able to get ultimate visibility across your entire IT ecosystem from a single, unified analytics platform with federated search.
Gurucul’s intelligent data fabric automatically ingests the data you need and starts detecting threats right away. It interprets, monitors, enriches, reduces and routes data from any source, format or IT estate, even non-security related data. You get full visibility and coverage without the need for costly third-party services, data distribution tools or parsing software.
Find true positives in real-time with our massive library of pre-tuned ML models that have been developed and refined for more than a decade to drive high-fidelity detections, decrease false positives and find zero-day threats. We go beyond basic anomaly detection and chain together identity, activity, and threat analytics to quickly detect and respond to known and unknown threats.
Our dynamic risk engine delivers a real-time prioritized view of business risk so that you can respond quickly to the greatest threats. A single, consolidated risk score is generated for any user, entity, application or asset group across every transaction and entitlement so you can trust scores and confidently take action. You can easily customize scores and thresholds to manage risk tolerance specific to your business.
Focus your limited resources on what matters most, quickly eradicating true threats. Augmented by AI, analysts can spend more time conducting worthwhile investigations and threat hunting using natural language and federated search while automating response with recommended playbooks from the platforms native SOAR solution.
Radical Clarity Drives Transformative Operations
A global IT Services company with a 70 person SOC team managing 250K users and 450K assets was being overran with SIEM alerts, until they turned to Gurucul.
Unique Design Principles
Gurucul’s dynamic security analytics platform offers differentiated features across the entire threat detection & response lifecycle. Our platform conforms to your business, so you don’t have to compromise.

Open and Flexible
Customer choice means you can use any data lake, ingest, search and analyze any data, deploy in any environment and integrate with your existing technology stack, all while maintaining the ability to rapidly scale.

Intelligent Data Fabric
Native data streaming normalizes, filters and parses any data source or format and extracts security-relevant context for optimized ingestion costs and improved detections.

Purpose-Built Content
A builder’s security analytics platform that’s loaded with content for fast time to value for those who need it to work out of the box, or can be customized to your unique business needs.

Advanced Analytics
Immediately detect risky behaviors and apply advanced ML-driven analytics in real-time to drive high-fidelity detections, decrease false positives and find zero-day threats on Day One.

Dynamic Risk Engine
Quantify security risk with a normalized 0-100 score, and deliver a real-time prioritized view of business risk, so that you can respond quickly to the greatest threats.

Powered By Artificial Intelligence
A native, secure AI engine that works across the detection, investigation and response lifecycle (TDIR) without compromising data privacy.
One Platform, a Plethora of Possibilities
The modular architecture of our security analytics platform means you can start where you’re at, unlock product capabilities aligned to immediate needs and scale up within a single platform as needed.
Ready to get a new outlook on security?
Our dynamic security analytics platform runs circles around the complex legacy solutions. Let us show you how.