TRADITIONAL THREAT DETECTION & RESPONSE BUSINESS CHALLENGES
As organizations evolve their networks and infrastructure based on digital transformation objectives, it leads to an expanding attack surface with numerous security gaps. The efficiency and sophistication of phishing and social engineering attacks makes it virtually inevitable that an initial compromise occurs.
In addition, threat actors are piecing together existing and new malware strains with different techniques to better evade current detection methods that are often siloed. Despite vendor claims, Endpoint Detection and Response (EDR), Network Detection and Response (NDR), and traditional Security Information and Event Management (SIEM), have proven insufficient to reduce mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR) – further extending attacker dwell time within an organization to several months.
While many of these solutions, including the current crop of Extended Detection and Response (XDR) solutions, claim some form of analytics, they are primarily focused on analyzing specific sets of telemetry. This includes endpoint, log, or network data, with underdeveloped capabilities across other necessary analytics. Worse, their claims of machine learning (ML) and artificial intelligence (AI) are just unadaptable, rule-based AI that can be broken down as fixed conditional patterns leaving them ineffective at adapting to and finding new and emerging attacks and variants.
GURUCUL OPEN XDR CAPABILITIES
The Gurucul XDR solution collects a wide variety of telemetry, correlation, and analysis of indicators of compromise for high-fidelity attack detection, prioritized investigation, and risk driven response. With Gurucul Open XDR technology, Security Operations Centers (SOCs) of varying skills and size gain the necessary visibility, context, and automation to identify attack campaigns in real-time and prevent damage within minutes.
-
-
- Intelligent, Telemetry-Based Analytics
Without customization, Gurucul Open XDR automatically ingests, correlates, normalizes and applies analytics to telemetry beyond just endpoint and network data. It analyzes endpoint, network application, cloud, IoT, identity, network, structured and unstructured data, and even unknown data sources with trained ML that adapts over time for automating threat detection. - Accelerated Threat detection
Gurucul incorporates User and Entity Behavior Analytics with intelligent telemetry-based analytics and and industry-leading 2500+ open, transparent, and customizable ML models to detect, predict, investigate, hunt, and remediate threats. It goes beyond just an individual threat, to identifying the full scope of the attack campaign early in the kill chain. - Prioritized Investigations
Gurucul automatically correlates and consolidates the relevant telemetry, provides link event analysis, and provides both incident-level and campaign level risk scoring to prioritize investigation efforts. These capabilities provide a high-level of observability all the way offering drill-down threat hunting for multiple experience levels.
- Automated Incident Response
Security staff can leverage automated response actions with risk-based triggers, orchestration playbooks, and automated incident timelines that create smart links of the entire attack lifecycle for pre- and post-incident analysis. The ability to visualize the entire kill chain and reconstruct the steps builds the necessary confidence in dynamically-created targeted response playbooks.
- Intelligent, Telemetry-Based Analytics
-
GURUCUL OPEN XDR – HOW IT WORKS
Gurucul Open XDR collects data from a broad cross-section of security telemetry, including endpoints, networks, servers, cloud platforms, applications, IoT, SIEM, identity sources, and more. The product collects, ingests, and enriches data from disparate sources on a massive scale without impacting performance. Ingested data from each of your systems is passed through a series of processing to optimize the information for different use cases, including threat hunting, triage, and investigation. Gurucul XDR unifies your disparate data logs and links them together with corresponding identity information.
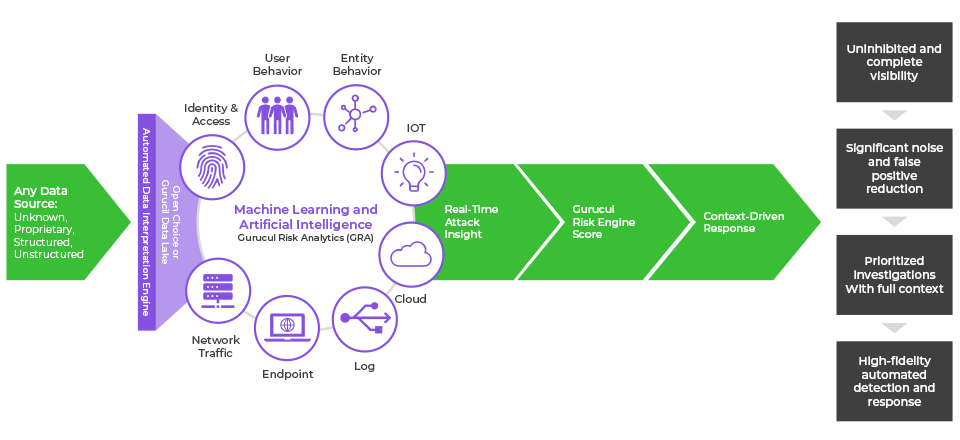
KEY BENEFITS OF OPEN XDR
Achieve immediate time-to-value through out-of-the-box automated threat detection in real-time
Adapt and more rapidly identify new threats and variants without the need for machine learning model updates from vendors
Eliminate manual customization needed for ingesting different data sources and reduce performance impact
Leverage and retain a correlated and normalized set of threat metadata that eliminates manual efforts
Drastically reduce MTTD to minutes or hours instead of days, weeks, and months through advanced detection
Elevate your security team to understand and respond more effectively to attack campaigns with targeted context and link event analysis
Accelerate response (reduce MTTR to hours) through risk-driven, dynamic playbooks with prioritized response actions
WHY GURUCUL OPEN XDR?
Organizations can significantly accelerate and drastically improve their teams’ ability to prevent successful breaches early in the kill chain with Gurucul’s data ingestion and correlation capabilities, the most comprehensive set of advanced analytics, and an industry-leading number of trained machine learning models, all consolidated into a single console.
Open XDR Use Cases
Accelerated Threat Detection and Response
Gurucul goes beyond endpoint-centric solutions with an advanced set of security analytics and detection across a wide variety of telemetry, including endpoint and security solutions. This accelerates and increases the overall efficiency of your existing security operations programs, tools, and resources. Gurucul Open XDR and SOAR technologies work together to automate manual tasks related to data collection, correlation and contextualization, detection, investigation, and response in order to lower MTTD and MTTR.
Contextual Threat Hunting and Investigations
Even as Gurucul automates detection of both known and unknown attacks and variants, security analysts still want the freedom to threat hunt and validate existing detections through investigations. Outside of prioritizing indicators of compromise, Gurucul provides a unified console that eliminates the overhead of logging into multiple systems to hunt and investigate potential threats. This approach allows analysts to see an overall understanding of attack campaigns impacting their organization at a high-level, with the ability to drill down further into granularity necessary for more experienced hunters.
Dynamic Playbooks for Automating Response
With Gurucul’s trained, open ML models, the platform provides a more targeted set of playbooks that includes the necessary context to work with broader security and IT teams to respond to threats. More importantly, Gurucul prioritizes response actions as part of the overall remediation effort and cleanup of the attack campaign. In addition to accelerating response time, this also eliminates the manual task of having to customize broad playbooks that without intervention could hamper availability of IT resources unnecessarily or that have unexpected results when implemented.
Detecting Identity-Based Threats
Identity is the new perimeter and therefore also a new attack surface. While most XDR solutions have been focused on the “what” or “how”, they miss the focus on understanding “the who” and how critical that is to preventing damage to an organization. Gurucul incorporates the most advanced set of identity analytics into our Open XDR, that goes beyond just Active Directory information. It baselines, monitors and analyzes access privileges, entitlements, and even peer comparisons to detect credential-based attacks. When you combine that with Gurucul UEBA, you get an even deeper view into both internal and external threats, such as supply chain attacks, much earlier in the kill chain to prevent damage.




