Clean up the access plane to dramatically reduce accounts, entitlements, and over-privileged access.
Gurucul Identity Analytics gives security teams dynamic risk scores and advanced analytics data that help inform provisioning, de-provisioning, authentication, and privileged access management.
Gurucul Identity Analytics helps security teams baseline current access privileges and policies—setting the foundation for an effective Zero Trust program.
From a single console, analysts can monitor for least-privileged access misuse, violations, and unsanctioned lateral movement—with outlier access and anomalous behaviors continuously ranked for risk and elevated accordingly.
Take advantage of Gurucul’s advanced machine learning models to define, review, and confirm accounts and entitlements for access—and get the most from your IAM, IGA, and other existing identity management systems.
The Gurucul big data platform gives security teams a true 360-degree view of identity analysis, access, privileged access, usage in the cloud, mobile, and on-premises.
With complete visibility into account activity and user entitlement information, security teams can streamline, track, and report on the entire user access review lifecycle—expediting certifications, cleaning up accounts and access entitlements, and reducing identity risk.
Automate reporting by leveraging hundreds of out-of-the-box reports that can be customized and scheduled to ensure compliance and enable inter-department collaboration.
REVEAL is the visionary security platform that delivers radical clarity into your cyber risk and drastically reduces data costs. It’s a unified suite of capabilities and tools that uncover true threats and quantify risks in real-time—regardless of the data source, across the entire IT estate.
REVEAL gives security teams the visibility, focus, and perspective they need to outpace threats and focus on what matters most.
REVEAL is the visionary security platform that delivers radical clarity into your cyber risk and drastically reduces data costs. It’s a unified suite of capabilities and tools that uncover true threats and quantify risks in real-time—regardless of the data source, across the entire IT estate.
REVEAL gives security teams the visibility, focus, and perspective they need to outpace threats and focus on what matters most.
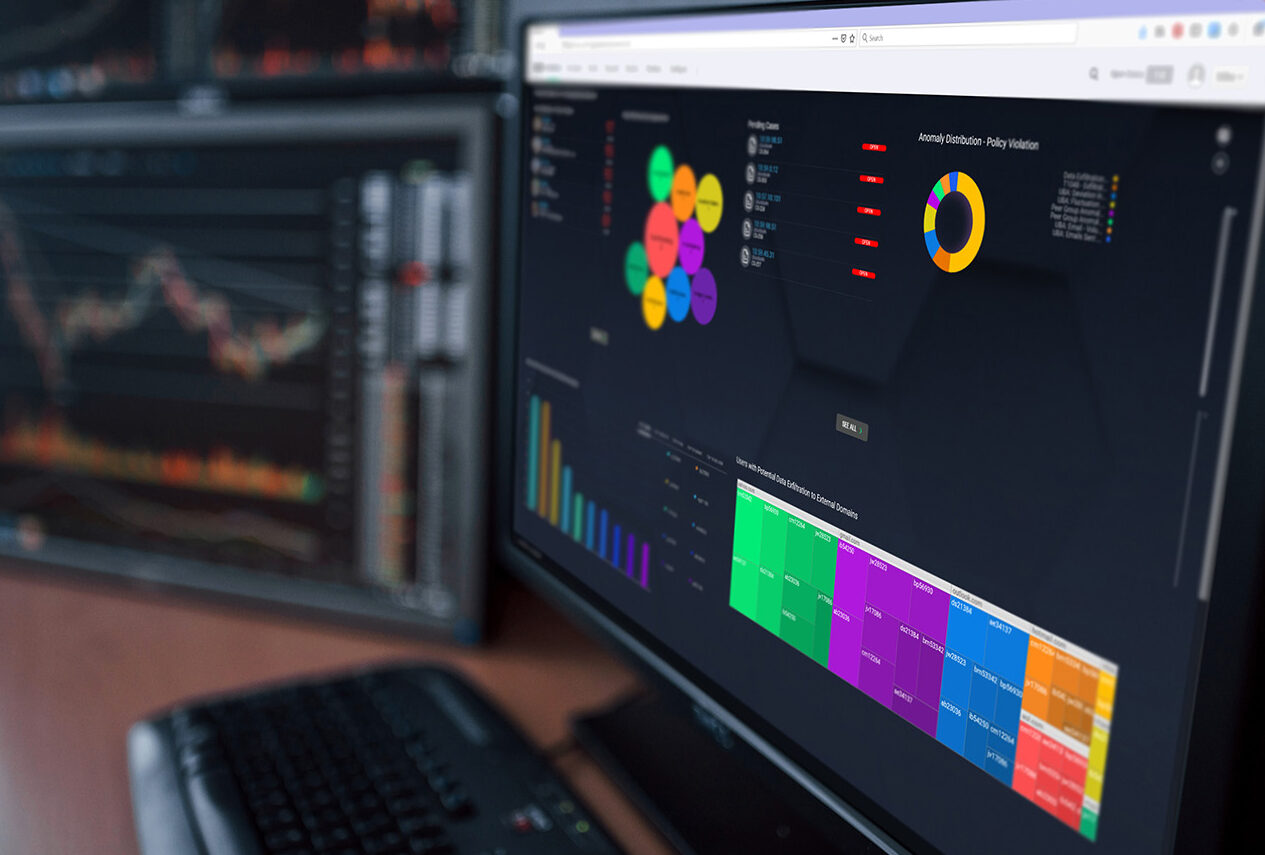
Reduce the risk of orphaned and dormant accounts being compromised or misused. Apply advanced analytics to identify them, reduce excessive entitlements, and eliminate access outliers.
Discover, risk-rank, and monitor accounts with privileged access for outlier access and anomalous behavior. Find who has elevated access with privileged entitlements within applications and unstructured data that exist or may have escalated after provisioning.
Reduce rubber-stamping, time spent, and overall risk through outlier certification. Identify and eliminate access not associated with job responsibilities and reduce potential account compromise risk.
Enable zero-day provisioning and automated approval workflows for higher risk access by inspecting inlier analytics. Import identities, accounts, and entitlements with metadata, trigger risk-based outlier access certifications, and provide closed-loop integration with access certification actions.
Prevent and detect Segregation of Duties (SoD) violations or toxic combinations of access and their usage. Automatically review existing roles and entitlements across systems and identify inter- and intra-application SoD risks.
Enable real-time risk-based access policy enforcement of authentication levels for user access to systems, devices, and applications.