 Sometimes the biggest risks to your organization live within and as history has shown insider threats can be devastating to business. This is where an insider risk management program becomes crucial for safeguarding your organization’s most valuable assets. Insider threats are hard to detect because they come from individuals with legitimate access to systems, making their actions seem normal. Identifying these threats requires spotting subtle deviations in behavior, which can easily go unnoticed without advanced monitoring tools.
Sometimes the biggest risks to your organization live within and as history has shown insider threats can be devastating to business. This is where an insider risk management program becomes crucial for safeguarding your organization’s most valuable assets. Insider threats are hard to detect because they come from individuals with legitimate access to systems, making their actions seem normal. Identifying these threats requires spotting subtle deviations in behavior, which can easily go unnoticed without advanced monitoring tools.
In today’s digital landscape, data security is paramount. Organizations must protect their trade secrets and confidential information internal threats. A compelling insider risk management program is crucial for maintaining security and compliance while safeguarding your most valuable assets.
Before diving into the intricacies of insider risk management, let’s discuss what constitutes an insider threat. An insider risk refers to a security risk that originates from within the organization. This includes current or former employees, contractors, third parties or business partners authorized to access an organization’s network, systems or data.
Insider risk management is a comprehensive approach to identifying, assessing, and mitigating potential threats posed by individuals within an organization. It involves implementing policies, procedures, and technologies to monitor and analyze employee behavior, protect sensitive data, and prevent unauthorized actions that could harm the company’s assets, reputation, or operations.
According to the 2024 Insider Threat Report from Cybersecurity Insiders, insider attacks are a growing concern for organizations, with 48% reporting that these attacks have become more frequent in the past year. Additionally, 51% of organizations experienced six or more insider incidents during the same period. The financial impact is also significant, with 29% of organizations indicating that the cost of remediation exceeded $1 million per incident.
Furthermore, the report highlights that 71% of organizations feel at least moderately vulnerable to insider threats, yet only 36% have a fully integrated solution for unified visibility across their environments. These statistics emphasize the need for stronger insider risk detection software and strategies that incorporate advanced detection technologies and provide necessary context across the entire insider risk lifecycle.
The rapid shift to remote and hybrid work has blurred the boundaries of the traditional workplace, making it harder to control and monitor employee activities. This evolution has increased the complexity of managing internal risks and protecting confidential information.
Meanwhile, cloud adoption has expanded the attack surface, increasing the likelihood of data breaches originating from within. These evolving dynamics create identity sprawl and privilege management complexity making insider risk a growing concern.
According to the Verizon 2023 Data Breach Investigations Report, 74% of all data breaches involve the human element, emphasizing the importance of monitoring insider activities. The Ponemon Institute’s 2022 Cost of Insider Threats Report reveals that incidents involving insider threats have increased by 44% since 2020. With these statistics in mind, organizations must adopt a proactive approach to quickly identify potential malicious activities with insider risk detection.
Key trends contributing to the rise of insider threats include:
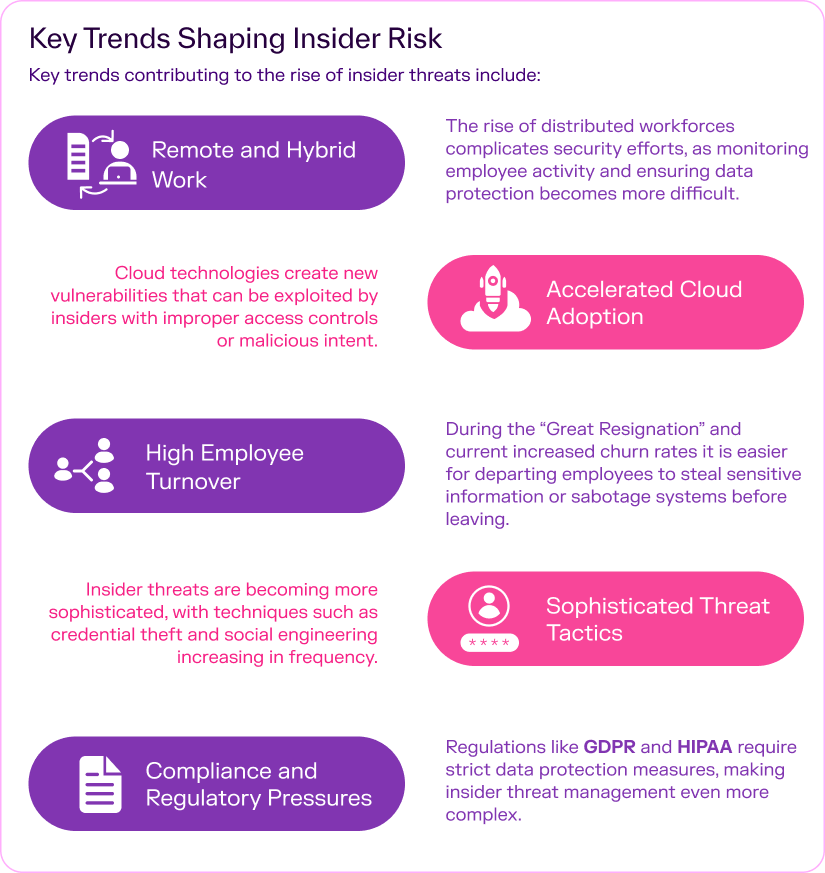
By leveraging Gurucul’s User and Entity Behavior Analytics (UEBA) platform, organizations can gain real-time insights into these trends with true insider threat detection software. Gurucul’s advanced analytics identify anomalous behavior and insider risk indicators, enabling organizations to detect and respond to threats before they escalate.
Given the potential for significant financial losses and reputational damage, implementing a robust insider threat program is no longer optional—it’s a necessity. A compelling insider risk management strategy helps detect and prevent insider threats and ensures compliance with various regulatory requirements.
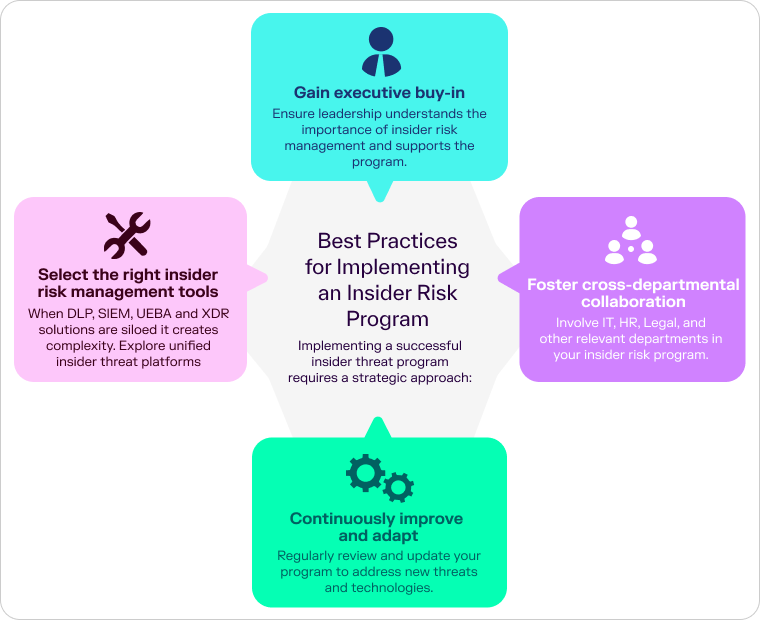
The foundation of any successful insider risk program is a thorough risk assessment. This involves identifying your organization’s critical assets, evaluating potential vulnerabilities, and assessing various insider threat scenarios. Understanding your risk landscape allows you to prioritize your efforts and allocate resources more effectively.
Clear, comprehensive policies are crucial for insider risk mitigation. These policies should outline acceptable use of company resources, data handling procedures, and consequences for policy violations. Equally important is effectively communicating these policies to all employees and ensuring they understand their responsibilities.
Creating a security-conscious culture is vital for insider threat prevention. Regular training programs should educate employees about insider risk indicators, reporting procedures, and best practices for data protection. This helps prevent accidental insider threats and creates a vigilant workforce that can identify and report suspicious activities.
Implementing the principle of least privilege is a cornerstone of insider risk detection. By limiting access to sensitive information and systems to only those who need it for their job functions, you can significantly reduce the risk of insider threats. This Zero Trust approach is never set it and forget it, which requires robust Identity Analytics (IdA) to maintain identity hygiene and reduce identity sprawl.
The ability to monitor users and entity behavior with UEBA solutions is critical for any insider threat security management program. These solutions establish baselines to identify abnormal behavior that may indicate a potential insider threat. However, this can lead to a significant amount of false positive alerts, because not all anomalies are risks. It’s critical these solutions use machine learning analytics to contextualize behavioral deviations with all other surrounding telemetry allowing your insider threat team to predict, investigate and respond to only true threats.
Protecting sensitive data is crucial in insider risk management. This involves:
Effective insider threat programs do not operate in silos due to the sensitivity around employee privacy. The management of insider risk includes the organization’s Security, Human Resources, Legal and various lines of business. While the security function is usually tasked with the monitoring and detection of insider threats, it must build strong cases of evidence and work cross-functionally to conduct necessary investigations and respond accordingly. Responding to insider risk.
Despite best efforts, insider risk incidents may still occur. A well-defined insider risk incident response plan minimizes damage and ensures a swift, effective response. Regular drills and simulations ensure your team is prepared to handle various insider threat scenarios.
To ensure the effectiveness of your insider risk program’s effectiveness, establishing and monitoring Key Performance Indicators (KPIs) is crucial. These may include:
| Activity Based KPIs | Outcome Based KPIs |
| How many true insider threats were detected? | How many insider threat incidents were reduced? |
| How many cases were opened and reviewed? | How many policy violations were reduced? |
| How many cases were escalated internally or externally? | How much did your average time to detect and respond to incidents decrease? |
| How many suspicious activity reports were received? | Can you attribute monetary value to a reduction in incidents? |
| How many employees completed their training? | How much did employee security awareness certification success rate improve? |
Regular audits and assessments help identify areas for improvement and ensure your program remains effective against evolving threats.
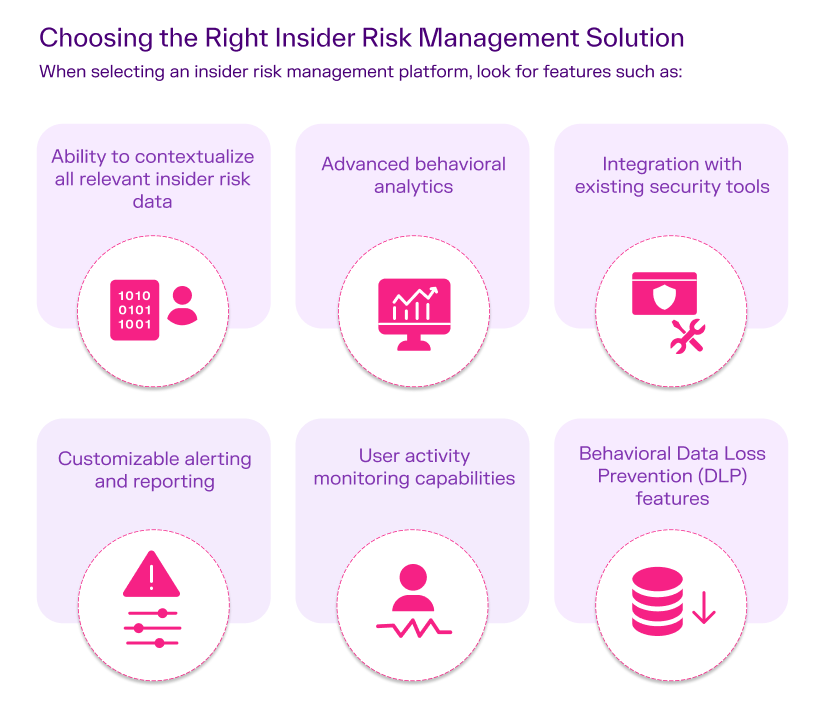
Gurucul’s insider threat management solution offers these features, providing a comprehensive approach to insider risk management. Our platform leverages artificial intelligence and machine learning to detect and prevent insider threats in real time, helping organizations stay one step ahead of potential risks.
In an era when insider threats pose a significant risk to organizations, implementing a robust insider risk management program is no longer optional—it’s a necessity. Organizations can significantly reduce their risk and protect their most valuable assets by understanding the nature of insider threats, implementing comprehensive strategies, and leveraging advanced technologies.
Don’t wait for an insider risk incident to expose vulnerabilities in your security posture. Take proactive steps today to evaluate and enhance your insider risk program. With Gurucul’s advanced insider threat management solutions, you can confidently safeguard your organization from threats from within.
Ready to improve your insider threat management? Contact Gurucul today for a personalized demo of our industry-leading insider threat detection and prevention solutions.
