Similar to most industries during the pandemic, K-12 public schools have been heavily targeted by threat actors with the shift to a remote operating environment. K-12 public schools are a $760 billion sector that serves more than 50 million students at over 100,000 schools across the United States.
School districts manage a wide set of IT infrastructure, software, and associated users, including students, faculty, and administration. Unfortunately, most do not have a dedicated cybersecurity team to handle security issues.
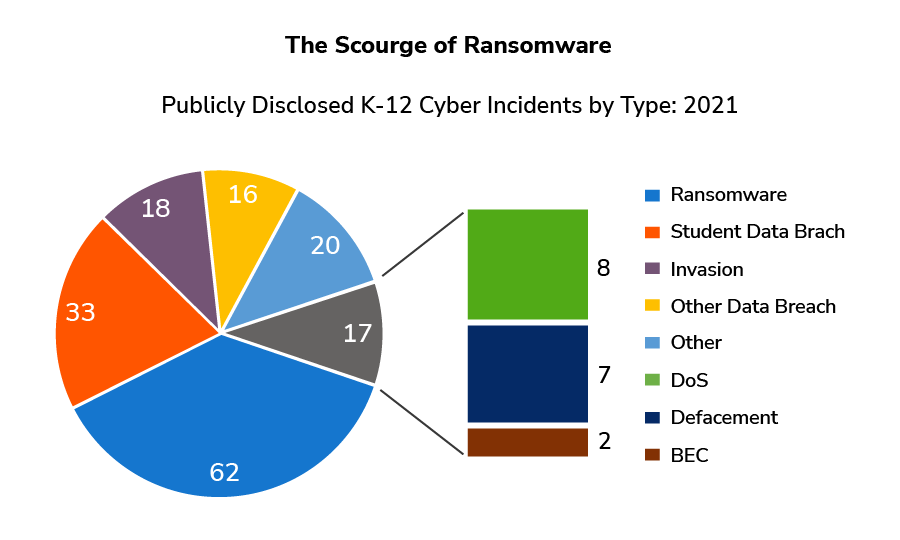
One of the most damaging security threats has been ransomware. In fact, the Buffalo, NY school board approved spending nearly $10 million on external IT consultants to help them respond to a ransomware attack it suffered to restore their data in March 2021. Certain states have regulations against public institutions from paying ransomware at all. In this case, the ransom was not paid, but the cost was extremely high regardless.
Typical ransomware demands made by threat actors against K-12 schools have ranged from $5,000 to $40 million, with an average payment of $268,000, according to Comparitech. This number has only gone up with current data across 2021-2022.
Source: State of Cybersecurity K-12 Year in Review, 2022 Annual Report by K12SIX
Between 2021 and 2022, 56% of K-12 education organizations were hit by ransomware, a nearly 25% increase from the previous year. Even with the return to in-person education, students are using a broader set of internet-connected devices at home and in school. Even worse is that home-networked devices can cross-infect school approved devices for home use, thereby infecting educational infrastructure and providing a gateway for a ransomware attack.
The E-Rate, or Education Rate, is a U.S. Federal program that provides schools, libraries, and consortia funding services related to internet connectivity, access and basic network security per the Federal Communications Commission (FCC).
On September 14, 2022, the Los Angeles Unified School District sent a letter to the FCC to update the program to help K-12 schools bolster their cyber security posture. This has been an ongoing request by many schools and agencies over the last 12 to 18 months.
However, the Los Angeles Unified School District, one of the top two in the country, suffered a ransomware attack in September, that caused disruptions to critical systems and shut down access to more than half a million users, which prompted this latest request.
“School districts with limited cybersecurity capabilities and constrained resources are often the most vulnerable; however, the opportunistic targeting often seen with cyber criminals can still put school districts with robust cybersecurity programs at risk” – the FBI, the Cybersecurity and Infrastructure Security Agency, and MS-ISAC.
While every enterprise and government sector has struggled to hire and maintain security talent, K-12 has especially struggled to build and/or maintain dedicated security resources. At least there has been increased, though inconsistent, emphasis on training for teachers on how to avoid phishing or ransomware scams. However, all it takes is one well-crafted email to trick someone into clicking a link.
As the cyber security market continues to evolve there is a lot of hype and promises that have been introduced making it difficult for security and certainly non-security practitioners to take the necessary steps to prevent a ransomware attack from successful detonation. In a nutshell, K-12 IT and Security Teams need to research and evaluate the most visionary SIEM and XDR solutions for:
Bottom line: K-12 organizations need more context, more automation, and faster answers to shut down ransomware before it can get a foothold.
To learn more about how Gurucul offers better capabilities and value with a simpler and more automated Next Generation SIEM, visit our Next Gen SIEM product page. We have the technology. Let us help!
