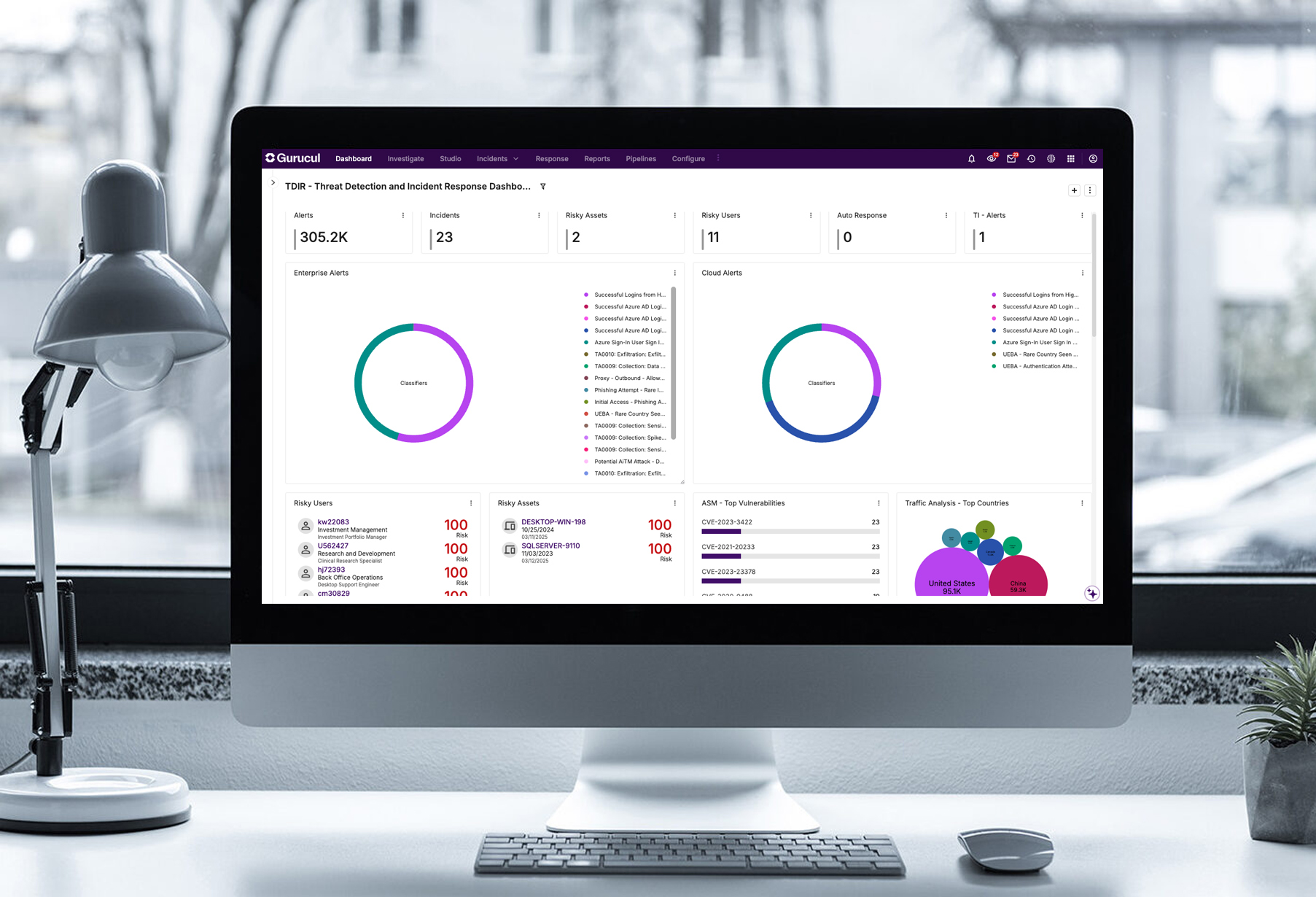
Ingest and analyze all relevant data and get radical clarity into your cyber risk with complete visibility and 360° context.
Gain full control over your data fabric with intelligent AI informed parsing, normalization, enrichment, filtering and routing that reduce costs by at least 40%.
Amplify analysts with an AI-centric experience across the entire SecOps lifecycle—so they can spend more time mitigating real risks.
REVEAL is an open and adaptable big data security analytics platform designed to handle the most demanding workloads at speed and scale.
It’s data lake and cloud-agnostic, so you can build a centralized or federated architecture using Gurucul’s Hadoop data lake or bring your own. And it’s designed with flexibility in mind—meaning you can integrate and customize to best suit your business processes, tech stack, and deployment requirements (On-Prem, Cloud or SaaS).
No matter what, REVEAL gives you control—helping you eliminate the myriad data costs and scalability issues inherent to traditional SIEMs and siloed cyber security analytics solutions.
The REVEAL security analytics platform includes a native AI Data Engine that autonomously filters, normalizes, enriches, routes, analyzes, and searches any security, non-security, and IT Ops data from any source to start detecting threats right away—giving you complete control over your security data fabric and reducing costs by at least 40%.
Take advantage of out-of-the-box features like AI-powered data parsing, monitoring and alerting—along with the built-in no-code four-step pipeline wizard—to make any new data source accessible and visible in minutes.
With REVEAL, analysts get ultimate clarity into the entire hybrid IT ecosystem delivered on a single, unified platform—without the need for third-party services, data distribution tools, or parsing software.
The REVEAL security analytics platform is ready out-of-the-box with 10,000+ pieces of content—so you can go from ingestion to high-fidelity detections in seconds.
Plus, any pre-built content is fully customizable, so you can modify and create virtually infinite configurations using flexible dashboards, ML models, risk scoring, playbooks, and more.
Get value and ROI on day one, and then customize at your pace to meet your specific business, security, or compliance requirements.
The REVEAL security analytics platform goes beyond basic anomaly detection. Drawing from a massive library of pre-tuned ML models developed and refined over more than a decade, REVEAL automatically applies a wide range of behavioral analytics to structured and unstructured data from endpoints, network applications, the cloud, or IoT— including IT Ops and non-security data.
Analysts are empowered with a single console that is infused with AI insights across the entire threat lifecycle with 360° threat context to accelerate triage, investigations and response.
Go one step further and chain multiple ML models together using different sources like identity, activity, and threat intelligence to drive higher-fidelity detections, fewer false positives, and find more zero-day threats.
The REVEAL security analytics platform quantifies and elevates risk on a normalized scale of 0–100, so security teams can quickly and easily understand and prioritize the top threats to the business.
Analysts can see a consolidated risk score for any user, entity, application, or asset across every transaction, entitlement, and activity—and then take decisive action using a library of fully customizable response playbooks configured to your organization’s unique criteria and workflow.
With just a few clicks, security teams can easily customize risk scores based on defined risk tolerance—so analysts know where to focus time and attention.
REVEAL even allows teams to create custom groups for critical or sensitive entities like executive laptops, contractors, database servers, or critical business applications—and then elevates risk scores to help analysts respond when these groups are impacted.

External Threats
Give analysts a comprehensive, real-time view of true cyber threats in complex hybrid or multi-cloud environments with proactive, risk-oriented Threat Detection, Investigation and Response tools.

Insider Risk
Proactively monitor for and stop insider risks before they become a threat. Armed with context-aware data on real-time detections, analysts can collaborate with HR and Legal to proactively mitigate risks.

Identity Threats
Protect your identity attack surface by adopting an identity-centric approach to threat detection and revoke access before attacks can occur. REVEAL gives security teams visibility and contextualized insight into risky access behavior and suspicious activity within identity systems.
Mathan Kasilingam, CISO & Data Privacy Officer – Vodafone Idea Limited
VP & Head of CyberSecurity Technology Operations – Global IT Services Company
Learn the basics about REVEAL, drill down into the platform's unique features, or take a guided tour from an analyst's perspective. It's all here in the Demo Hub.