
The proliferation of IoT in healthcare, while revolutionizing patient care and operational efficiency, has exponentially expanded the attack surface for ransomware threats, making robust cybersecurity measures more critical than ever.
The American Hospital Association reports that healthcare cybersecurity threats continued unabated last year, with more than 385 documented attacks against medical facilities and critical service providers. While these numbers mirror the historic highs of 2023, the AHA emphasizes that this year’s incidents have inflicted notably deeper impacts across the healthcare ecosystem, surpassing previous patterns in both scope and severity.
Building on these alarming statistics, the healthcare sector faces an escalating threat from ransomware attacks specifically targeting medical devices. These attacks not only compromise patient data but also pose direct risks to patient safety by potentially disrupting critical care equipment. The interconnected nature of modern medical devices within hospital networks creates a vast attack surface, making them particularly vulnerable to ransomware.
As cybercriminals increasingly recognize the life-or-death leverage they hold over healthcare providers, the potential for catastrophic outcomes and the pressure to pay ransoms have never been higher, underscoring the urgent need for robust cybersecurity measures in medical technology. Do you want to learn more about the importance of cybersecurity in healthcare? Check out our blog, “Cybersecurity for Healthcare: Protecting Patient Data in the Digital Age.”
The threat of medical device ransomware attacks stems from changes in manufacturing. In recent years, manufacturers began including popular operating systems (OSs) on these devices. Formerly, medical devices used proprietary firmware or other exclusive features. That meant medical devices were rarely targeted in cyberattacks. The attacks simply didn’t pay off for criminals. Developing targeted attacks against these specialized devices was not as simple – or lucrative – as targeting mainstream systems.
But now manufacturers are building medical devices running Windows (and other popular OSs). The obvious benefit of running a standard operating system is that it’s easier for IT to apply patches. But there are also drawbacks. Healthcare ransomware attacks previously only seen on servers and desktops, now inflict medical devices as well.
Mitigating these attacks is especially critical in healthcare where the stakes are high. In most healthcare ransomware attacks, an organization might lose valuable data. But attacks on medical devices can put lives at stake.
So how can you ensure medical device security? One way is to understand their behavior patterns. For example, medical devices generally have a specific purpose. Their usage patterns typically don’t change much. Once you know these standard behaviors, you can identify unusual trends that could indicate the device has been compromised.
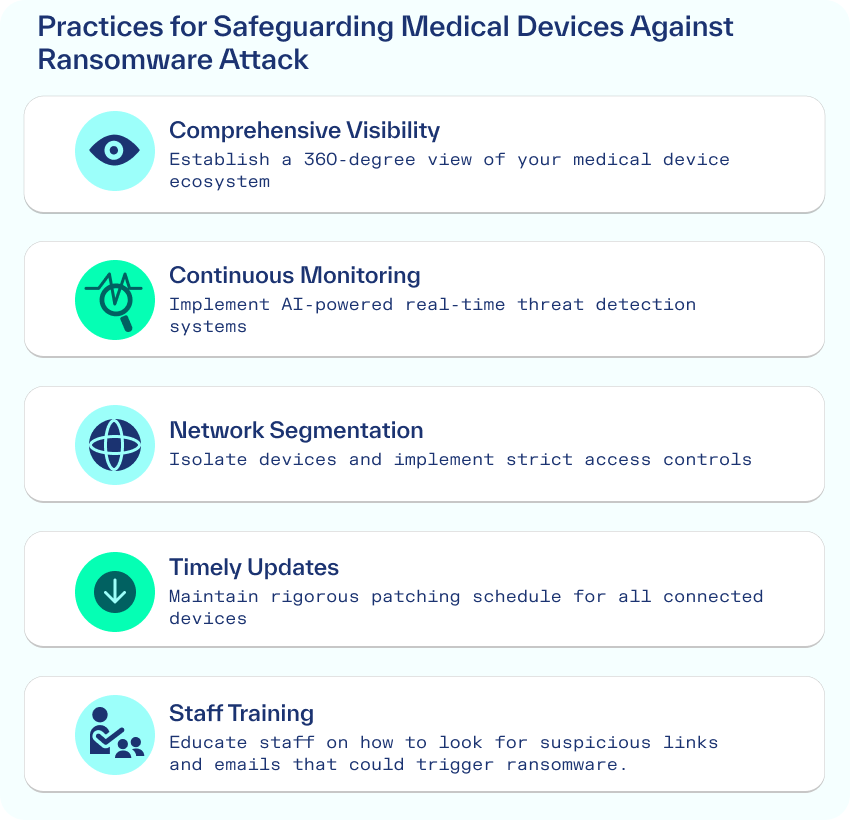
In an era where healthcare ransomware attacks are surging, protecting medical devices from cyber threats has become paramount. The increasing frequency of medical device ransomware incidents demands a proactive approach to cybersecurity in healthcare settings. Here are essential strategies to fortify your medical infrastructure against these malicious attacks:
Don’t let cybercriminals exploit blind spots in your healthcare network. Leverage advanced security analytics platforms like Gurucul UEBA to establish a 360-degree view of your medical device ecosystem. This visibility is crucial for detecting anomalous activities that could signal an impending ransomware attack on medical equipment.
Stay ahead of evolving healthcare cybersecurity threats. Employ real-time monitoring solutions powered by AI and machine learning to analyze device behaviors continuously. Gurucul’s REVEAL security analytics platform goes beyond basic anomaly detection, applying sophisticated behavioral analytics to identify potential ransomware threats before they compromise critical medical devices.
Contain the spread of potential healthcare ransomware infections by isolating medical devices on separate network segments. Implement rigorous access controls and adhere to the principle of least privilege, ensuring only authorized personnel can interact with these life-critical devices, reducing the attack surface for ransomware actors.
Seal vulnerabilities before cybercriminals can exploit them. Maintain a stringent patching schedule for all connected medical devices. Utilize Gurucul UEBA’s insights to identify safe maintenance windows when devices are out of rotation, minimizing disruptions to patient care while keeping systems resilient against the latest ransomware variants.
Empower your healthcare team as the first line of defense. Conduct regular cybersecurity training sessions focused on the unique challenges of medical device security and the growing threat of ransomware in healthcare. Ensure staff understand the potential impact of ransomware on patient care and their crucial role in preventing attacks.
Prepare for worst-case scenarios to ensure optimal outcomes. Develop and regularly test a comprehensive incident response plan tailored to medical device ransomware scenarios. Integrate Gurucul’s SOAR capabilities to automate and streamline your response processes, minimizing the impact of potential healthcare ransomware attacks.
Implement ironclad backup solutions for medical device data and configurations. Regularly test restoration procedures to ensure rapid recovery during a ransomware attack, minimizing downtime and potential impact on patient care. This strategy is crucial in mitigating the effects of healthcare ransomware incidents.
Partner with medical device manufacturers who prioritize cybersecurity. Conduct thorough security assessments of devices before deployment and collaborate closely with vendors to promptly address any identified vulnerabilities that could be exploited in ransomware attacks.
By implementing these best practices and leveraging advanced security analytics solutions like Gurucul’s platform, healthcare organizations can significantly enhance their defense against the rising tide of ransomware attacks targeting medical devices. In the healthcare industry, robust cybersecurity measures are not just about protecting data but about safeguarding lives and ensuring uninterrupted patient care.
In the healthcare industry, patients must always come first. The prospect of a patient being harmed due to a faulty medical device behavior is not as far-fetched as it may seem. UEBA’s ability to establish baseline behavior profiles to ensure medical device security holds great value for healthcare organizations.
Our User and Entity Behavior Analytics (UEBA) solution establishes baseline behavior profiles. From there you can detect activities that are outside the normal patterns. When a medical device acts irregularly, there are only a couple of reasons why. Either the device malfunctioned and needs to be serviced, or it was compromised. This anomalous behavior triggers our UEBA solution’s risk-based alerts. The alerts could mean, for instance, someone accessed the device and changed its configuration. In other words, it’s been hacked.
UEBA can also benefit healthcare organizations from an IT management perspective. It’s not uncommon to see new medical devices pop up on the hospital network. In these shadow IT situations, the apparatus is usually procured by a physician or a hospital organization with their own discretionary budgets.
Watch the video Allina Health Gurucul Customer Story: Monitoring Medical Devices” to hear the Allina Health CISO describe how Gurucul’s security analytics technology secures the medical devices on their hospital network.
This situation resembles the general IoT use case that any enterprise might deal with. However, the medical device use case introduces additional degrees of complexity. A device may report that it’s malfunctioning and must be swapped out for a new unit. From the IT perspective, that’s one device leaving and one device entering the network. With Gurucul UEBA you can know when a replacement device is performing differently than the typical behavior of those devices. Being aware of this issue and taking immediate action is essential.
Another challenge with medical device security is knowing when to safely patch or service the device. There’s a risk that the patching process might take the device down or disable it. The IT team can’t patch or update a device at will. The device might be performing a clinical service at that time. With UEBA it’s possible to know when a device is out of rotation. And that lets you know when it’s safe to perform maintenance.
For example, UEBA can tell us that a particular device is out of use between the hours of 8 PM and 6 AM. With this knowledge, you can perform maintenance during those off hours so as not to interfere with patient care.
In today’s escalating healthcare ransomware attacks, Gurucul offers a cutting-edge cybersecurity platform tailored for the healthcare industry. Our solution provides unparalleled protection for medical devices, patient data, and critical infrastructure.
Key features include:
Don’t let ransomware compromise your medical devices or patient safety. Empower your security team with Gurucul’s advanced cybersecurity for healthcare solutions and focus on delivering exceptional, uninterrupted patient care in a secure digital environment. Our cutting-edge platform revolutionizes healthcare cybersecurity, ensuring your organization stays ahead of evolving threats while maintaining compliance and operational efficiency.
In the healthcare industry, patients must always come first. The prospect of a patient being harmed due to a faulty medical device behavior is not as farfetched as it may seem. UEBA’s ability to establish baseline behavior profiles to ensure medical device security holds great value for healthcare organizations.
Learn more about Gurucul’s unique healthcare cybersecurity solutions for medical device discovery and monitoring. Then, request a demo to see our UEBA platform in action.
