Limitations of Traditional and Second Generation SIEMs
Why is a Next Generation SIEM better than a Traditional SIEM?
Supports Cloud-Native, Hybrid and Multi-Cloud Deployments
Provides Complete Observability
Supports Big Data Architecture
Offers Better Threat Detection through Automation
Facilitates Prioritized Investigations
Enables Dynamic Threat Remediation

In this blog we detail the evolution of Next-Gen SIEM. Traditional SIEMs have primarily been used to improve network visibility and cyber security while supporting compliance. They ingest, collect, and store log data across applications, networks, and systems. SIEMs make it easier to capture and search for data that helps organizations when it comes to audits, forensics, and incident response. Because it serves as a central data repository that can provide visibility across the enterprise, it is often used by the security operations center (SOC) as the primary console for identifying and investigating events that are indicative of an active threat and attack campaign. The “S” in SIEM has been maturing for several years now.
The early version of SIEMs had mediocre search capabilities that made it very difficult to retrieve data that was collected over time. Administrators were able to perform simple correlation that enabled them to group together related data based on time and/or IP address. While this was helpful, the second generation of SIEMs have dramatically improved the searchability issue but stop short of true security analytics. Some have tried to add these technologies. However, fundamentally these platforms are designed for on premise log collection. Adding new analytic capabilities like Network Traffic Analysis, Network Detection and Response (NDR), or User Entity Behavior Analytics (UEBA) is almost impossible, so these technologies are ‘bolted on’ as opposed to truly integrated.
This is also true for the cloud. Today’s move to hybrid cloud, de-centralized cloud, and multi-cloud environments requires a full re-architecture of the SIEM. Traditional and second generation SIEM platforms cannot adequately invest in rebuilding an entirely new product. So they try to “MacGyver” it to work in the cloud. However, most are unable to handle the volume required and/or provide full visibility without manually correlating multiple installs. Newer cloud-native products lack the functionality of traditional SIEMs.
This has led to a sharp rise in the flood of events, false positives, and manual efforts SOC analysts encounter when figuring out if a threat is real, if an active campaign is underway, or how to respond in a timely and precise manner. When it comes to threat detection, investigations, and response, the traditional SIEM underdelivers.
A true Next-Gen SIEM is designed as a cloud-native SaaS platform that works reliably in de-centralized, hybrid, multi-cloud environments. It can accept a wider variety of telemetry, including application, network endpoint and cloud along with threat intelligence. It offers a unified set of analytics, trained machine learning (ML) and artificial intelligence (AI) for accurate detections; gathers context that is related to the attack to prioritize and validate the attack campaign (investigation); and, has dynamic response capabilities for faster, and more precise remediation. The following requirements outline the capabilities a cloud-native SIEM should provide to meet the needs of today’s modern infrastructures:
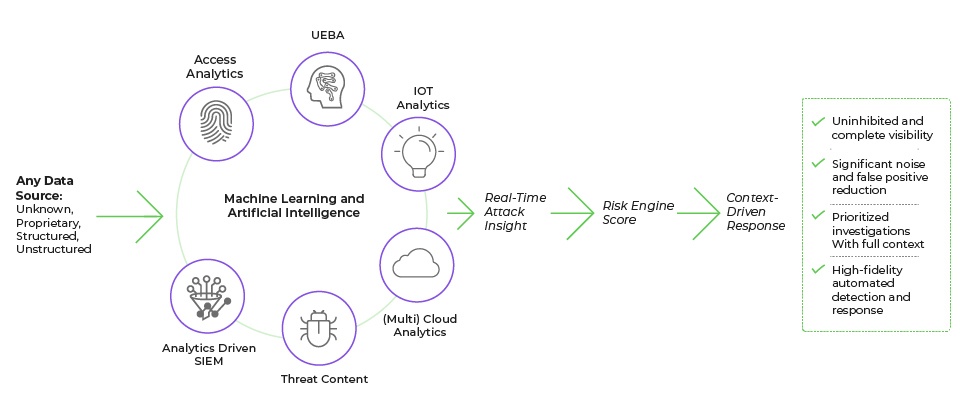
A Next Generation SIEM must be purpose-built to operate in a variety of public and private cloud environments, which includes AWS, Microsoft Azure, GCP, and others. This includes the ability to seamlessly manage and support data requirements across geographically dispersed clouds (also known as “federated search”). This must also be true for hybrid environments as most enterprises will still maintain data in the cloud and on-premises.
Supporting multi-cloud environments goes beyond just collecting data from the cloud. The SIEM must support the ability to properly gather data and apply advanced threat analytics across multiple clouds to identify threats that hide across public cloud environments.
Many SIEMS have difficulty ingesting and consolidating data across the enterprise at scale due to their fundamental architecture and/or data-based licensing model. Yet it’s critical to be able to send data to the SIEM from other security solutions, applications, endpoints, network packet information, etc., to gain a holistic view of the environment.
In addition, most SIEM and XDR solutions are rules-based ML/AI engines. A true Next-Gen SIEM uses trained machine learning, which provides better results than rules-based ML/AI because it ingests a wider variety of data sources rather than a fixed set. This allows any analytics supported by ML/AI to pinpoint an attack much earlier in the lifecycle instead of waiting for a rule to trigger. In addition, trained machine learning detection models are much more effective at finding new attacks and variants that easily evade rules-based systems.
Because a SIEM is the “source of truth” for the SOC, it is in a perfect position to provide context on users, applications, networks, devices, and events in virtually all IT systems across the organization. Traditional SIEMs fail to work well with large scales of data and can also produce a high percentage of false positives, especially when an enterprise moves to the cloud because it generates a lot more events than on-premises solutions.
Conversely, a Next Generation SIEM should scale to handle a larger number of data sources, increased data volume, the ability to search security-related data sets, and continuous monitoring and analysis. The capabilities, along with incorporation of third-party threat intelligence feeds, fuel the ability to detect more sophisticated attacks.
A Next Generation SIEM offers a set of unified analytics that can be chained together, often referred to as model chaining, with the ability to analyze the chain. Model-chained analysis eliminates ambiguity in determining a threat through the cross-validation of the alerts. For example: You see early warning of risky behavior combined with unusual lateral movement. Then, there are potential command and control (C2) communications, plus geo-location concerns. This data is unified with context to establish a true threat. With traditional SIEMs, it can take days or weeks for security teams to gather all the context necessary and manually validate the various events as part of an attack campaign. For security teams to truly respond and prevent a breach, they must piece information together as quickly as possible to establish whether a targeted attack is taking place.
Most SIEMs and Security Analytics platforms simply correlate attack stages increasing the level of risk. They provide indicators of compromise for each attack stage or for whichever data source was used to trigger an event, but it is up to the analyst to determine if the included set of alerts is relevant to the attack or not.
A Next-Gen SIEM must have the ability to provide unified data sets across any data source. Combined with a wide breadth of analytics, it can provide the necessary context, which alleviates much of the manual effort it takes security teams to perform the investigation and confirm the validity of the attack campaign. As mentioned previously, the ability to chain analytical models together, cross-validate the attack campaign, and submit those results in an enterprise risk engine is critical to determining the priority of the attack. Conversely, most SIEMs simply rely on aggregated third-party risk scores versus generating a dynamic risk score that is specifically relevant to the organization.
For most SIEMs and associated SOARs, context and precision are lacking in response playbooks. Typically, they only offer guidance. The IT team must collaborate to come up with the right corrective action that fits the organization, which slows down response time.
A Next Generation SIEM must gather a full set of “relevant” context across the right sets of telemetry to provide accurate details about the attack, which leads to a precise set of actions for stopping a breach. It’s important to move away from static playbooks to generate a dynamic response rather than customizing static response actions, which can slow down remediation.
In addition, a Next-Gen SIEM must have the ability to prioritize individual actions in order to minimize business disruption and provide steps for a targeted response. Prioritizing actions based on risk enables security teams to take necessary steps to stem or limit the attack rather than waiting to take all actions at once.
A Next Generation SIEM must support and improve upon the most common use case for traditional SIEM – regulatory compliance. This happens through centralized compliance auditing and reporting that supports the entire business infrastructure. A Next Generation SIEM should have built-in support and reporting for common compliance mandates and standards, such as the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI DSS) and the Sarbanes-Oxley Act (SOX), NIST, GDPR, MITRE Attack frameworks, etc.
A true Next-Gen SIEM improves every stage of security operations. It’s meant to solve all the use cases pertaining to observability, compliance, auditing. It also accelerates accurate threat detection, investigation, and response.
Gurucul offers an award-winning Next Generation SIEM that is recognized by industry analysts as being the most innovative in its ability to address the needs of the market today beyond what other solutions can do. Contact us for more information or request a demo now.
About The Author
 Amol Bhagwat, VP, Solutions and Field Engineering, Gurucul
Amol Bhagwat, VP, Solutions and Field Engineering, Gurucul
Amol is a distinguished security professional with a strong consulting, implementation and leadership experience. As a part of the executive leadership team, he drives product strategy, marketing campaigns, solutions development, APAC technical sales and global customer success program. Amol brings over 15 years of experience in delivering security and risk management solutions for Fortune 500 customers across the globe. Prior to Gurucul, he played an important role in building security practice for one of the major global system integrator. He achieved exponential business growth as a practice lead with focus on innovative solutions and delivery excellence. Amol graduated from University of Mumbai with B.E. in Electronics.
